


 11.3.3.1 Using the smitty
mkpq Command
11.3.3.1 Using the smitty
mkpq Command


 11.3.3.1 Using the smitty
mkpq Command
11.3.3.1 Using the smitty
mkpq Command
Trying to find out why print jobs from a remote client get lost on the way to a server can be a frustrating problem. In this section, some common errors, as well as how to trace a job sent by a remote client using the iptrace facility, is discussed.
If you attempt to send a print job to a remote print server whose lpd daemon is down, you will receive the following message:
0781-374 Connection to server timed out after retrying rembak:errno=79: A remote host refused an attempted connect operation
To correct this problem start the lpd daemon on the remote system using
startsrc -s lpd
If you have a queue, finprt or fin2, on a client
system, sv1051c, and the host name for that client is not in the /etc/hosts.lpd
or the /etc/hosts.equiv file then you will receive a 0781-202 error
message when the lpstat command is run. See
Figure 110 for an example of the command output. This
problem is also seen with name server and routing problems.
# lpstat Queue Dev Status Job Files User PP % Blks Cp Rnk ------- ----- --------- --- ------------------ ---------- ---- -- ----- --- --- finprt @sv11 READY finprt: 0781-202 your host does not have line printer access. lpforu lp0 READY fin2 @sv11 READY fin2: 0781-202 your host does not have line printer access. # |
To correct this problem, you need to edit the /etc/hosts.lpd file on the
server and enter the host name of the client system as in
Figure 111.
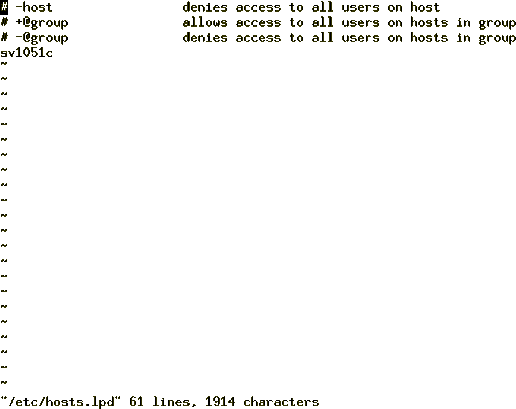
Figure 111: Content of /etc/hosts.lpd
The question, "What is getting sent to the remote system when I print?" can be answered by using remote trace.
The following list shows what an iptrace can tell you:
The iptrace facility can easily show what is being sent to the remote system using the following command:
Table 17 provides the iptrace command flags.
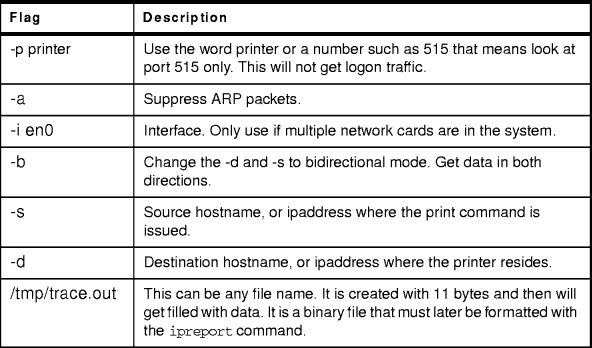
Table 17: Flags for the iptrace Command
enq -Pqueue_name filename
or use:
lpstat -vqueue_name
# ls -l /tmp/trace.out -rw-r--r-- 1 root system 4538 Nov 09 11:17 /tmp/trace.out
# ps -ef |grep ipt root 30984 1 0 11:17:47 - 0:00 iptrace -p printer -a -b -s sv1051c -d sv1166f /tmp/trace.out root 31234 26556 1 11:20:46 pts/10 0:00 grep ipt
kill -9 job_id
ipreport /tmp/trace.out > /tmp/report.out
The report contains three or four parts for each packet of data. These are:
The MAC header does not supply much information useful to debugging printing.
The IP header gives the direction of the data flow and the number of bytes in the packet, but direction is also given in the TCP packet.
The TCP packet gives the:
The data packets contain queue names, command information, actual data to be printed, print flags, and error messages back from the remote system lpd. It often simplifies the reading of the data to extract the data from the other packets. This is usually quite easy to do because all data lines of importance begin with at least four zeros. However when you do this, you corrupt the information about who sent individual packets.
grep 0000 /tmp/report.out > /tmp/datasent.out
The size of this file will largely depend upon the size of the data file being printed. For this reason, start with a small file. A useful command is:
echo "AAAAA" | qprt -Pqueue_name
This will show in the grep output as:
... 00000000 41414141 410a |AAAAA. | ...
You will notice that the data is divided into three columns. These are:
A PostScript output might look something like this:
!data hex equivalent of the characters ASCII equiv. of !byte in sent to the remote host the characters. !packet 00000000 020405ac |.... | 00000000 020405ac |.... | 00000000 0266696e 616c0a |.final. | 00000000 00 |. | 00000000 03313033 20646641 31303137 73763130 |.103 dfA1017sv10| 00000010 3531630a |51c. | 00000000 00 |. | 00000000 53746172 74207465 7374696e 670a5468 |Start testing.Th| 00000010 69732069 73206120 74657374 20707269 |is is a test pri| 00000020 6e74206a 6f622e0a 4920616d 20757369 |nt job..I am usi| 00000030 6e672069 70747261 63652074 6f207472 |ng iptrace to tr| 00000040 61636520 72656d6f 74652070 72696e74 |ace remote print| 00000050 206a6f62 732e0a46 696e6973 68207465 | jobs..Finish te| 00000060 7374696e 672e0a |sting.. | 00000000 00 |. | 00000000 00 |. | 00000000 02313038 20636641 31303137 73763130 |.108 cfA1017sv10| 00000010 3531630a |51c. | 00000000 00 |. | 00000000 48737631 30353163 0a50726f 6f740a66 |Hsv1051c.Proot.f| 00000010 64664131 30313773 76313035 31630a55 |dfA1017sv1051c.U| 00000020 64664131 30313773 76313035 31630a4e |dfA1017sv1051c.N| 00000030 53544449 4e2e3237 3535300a 2d4e310a |STDIN.27550.-N1.| 00000040 2d5a726f 6f744073 76313035 31630a2d |-Zroot@sv1051c.-| 00000050 74726f6f 74407376 31303531 630a2d54 |troot@sv1051c.-T| 00000060 53544449 4e2e3237 3535300a |STDIN.27550. | 00000000 00 |. | 00000000 00 |. | ...
The information gained from this output includes:
There is always an initial handshake protocol that seems to look like:
00000000 020405ac |.... 00000000 020405ac |....
The middle column always starts with 02 for the handshake part. The rest is identification information and doesn't matter in this discussion.
In general, lines like the following indicate a positive acknowledgment:
00000000 00 |. |
One of the first lines in the file is the queue name:
00000000 0266696e 616c0a |.final. |
Notice in the middle column that this begins with 02. This is a flag to indicate that this is the start of a print request. The name on the end of the line is the queue name.
A status request for a queue would start with an 03.The following binary identifiers are defined in the rfc.
A short distance down the file a line will contain the temporary file name:
00000000 03313033 20646641 31303137 73763130 |.103 dfA1017sv10| 00000010 3531630a |51c. |
In this case it begins with 03 in the middle column for data file. This is a subcommand of the receive a printer job command.
The receive printer job subcommands are as follows:
The preceding example line shows a receive data file subcommand with the following information:
The next packet of data from the client to the server is the data file itself. Check this file for extraneous characters, line feeds, spaces, tabs, and other things that might affect the format. The data in the right-hand column should be exactly what was on the client. As shown in the following example:
00000000 53746172 74207465 7374696e 670a5468 |Start testing.Th| 00000010 69732069 73206120 74657374 20707269 |is is a test pri| 00000020 6e74206a 6f622e0a 4920616d 20757369 |nt job..I am usi| 00000030 6e672069 70747261 63652074 6f207472 |ng iptrace to tr| 00000040 61636520 72656d6f 74652070 72696e74 |ace remote print| 00000050 206a6f62 732e0a46 696e6973 68207465 | jobs..Finish te| 00000060 7374696e 672e0a |sting.. |
The next packet from the client is usually the control file name, as shown in the following example:
00000000 02313038 20636641 31303137 73763130 |.108 cfA1017sv10| 00000010 3531630a |51c. |
The subcommand for control file begins with 02 in the middle column. The information from the receive control file is:
A sample control file excerpt follows:
00000000 48737631 30353163 0a50726f 6f740a66 |Hsv1051c.Proot.f| 00000010 64664131 30313773 76313035 31630a55 |dfA1017sv1051c.U| 00000020 64664131 30313773 76313035 31630a4e |dfA1017sv1051c.N| 00000030 53544449 4e2e3237 3535300a 2d4e310a |STDIN.27550.-N1.| 00000040 2d5a726f 6f744073 76313035 31630a2d |-Zroot@sv1051c.-| 00000050 74726f6f 74407376 31303531 630a2d54 |troot@sv1051c.-T| 00000060 53544449 4e2e3237 3535300a |STDIN.27550. |
The meaning of the control file format is shown in
Table 18.

Table 18: Control File Format